What is TOR network and browser?
The onion router(Tor) is a web browser that can access the internet using the Tor network. Tor project is an open-source network created by the government of the US to protect sensitive government communications over the internet in the mid-1900s. It was released under the free and open source license by the US Navy with some developments of original code. Since 2006 nonprofit organizations and volunteers have maintained the Tor network and browser for users. Tor networks use several layers of encryptions to protect your network traffic and it routs through a series of nodes that hide IP addresses, data, and browsing activities from the internet service providers (ISP) and other snoopers. Tot is used by journalists, whistleblowers, and others who want to protect their online privacy and anonymity. This is often used to access the dark web and provide onion web addresses (.onion) to preserve their anonymity and identities for websites and servers.
How does tor browser work?
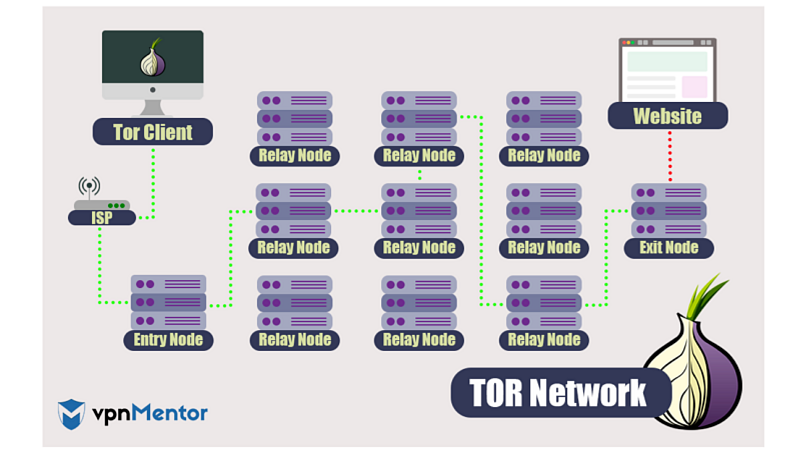
Tor encrypts your network traffic using several layers of encryption and the encrypted traffic is transmitted through a series of onion routers(nodes). While transmitting over the tor it decrypts layer by layer until it arrives at the final destination(remove all encrypted layers).
In a Tor network, there are three main nodes that are used to transmit the traffic through the Tor network.
01. Entry node: After successfully connecting with the Tor network, the browser randomly selects a public node to introduce your traffic to the Tor circuit it decrypts the first layer of encryption and selects a middle node to forward the traffic. This node is also known as the guard node.
02. Middle node: After passing the entry node your traffic passes through the series of middle nodes randomly selected by the last middle node. Each middle node removes the multiple encryption by decrypting the layer by layer of encryption until it reaches the exit node. while transmitting through middle nodes they do not know the IP address of the original requester. Tor network use more than 700 middle nodes to transmit traffic.
03. Exit node: The exit node decrypts the last layer of the encrypted data packet and sends it to the final destination by leaving the Tor network.
Tor hides your IP address, making it difficult to trace back your internet activity to you. The nodes hide your location details and identity other than your IP address. (This protects your details from ISP and the government) This anonymity enhancement process uses more time to open webpages or display results on the Tor browser. However, it is more safer.
This method is also used for hosting the onion websites.

0 comments:
Post a Comment