What can someone do with Ip address
An Internet Protocol (IP) address is a unique identifier that devices use to connect to the network. IP addresses function similarly to postal addresses, allowing information to be accurately directed to its intended recipient. It contains your device's geographical location details and your ISP. Devices use two types of IP addresses to communicate between devices. The local IP address is used to establish a connection in the local area network and the public IP address is used to identify you on the internet.
By getting access to an IP address hackers or someone else can have a potential effect on your identity. Let's talk about how they use IP addresses and what are those in the below.
Find your geographical location
IP location tracking is not an illegal activity. Most websites and services provide their services depending on your location. When you use a web service times you can see your county displayed some ware on the web page. That means they track your location using an IP address. Some of these websites customize the content according to your location. Also, some services could be restricted based on your location. That is called geo-blocking. At that time you can see a message like "This content is unavailable for your area". By using an IP address anyone can get details about your approximate geographical location including country, and nearest city. Once they know those details, they may be able to poke you by finding your actual address or location.
Show you personalized ads and spam
Online advertising services use tracking programs like tracking pixels, tracking URLs, and cookies. They collect data about how people interact with their ads. They take records of your IP address and your interactions on the internet. The scammers use your browsing history, location, and many tracking details to decide your interests. Some trackers send spam emails to their targets and collect more sensitive information about them to cheat on them.
Track online activity
Each IP provided by the ISP is assigned a user. The progress of any IP users can be tracked by the ISPs. Many employers, especially with the advent of telecommuting, will try to track your activities through your IP addresses. As an example, while you connect to a work network, Employees can track everything you do online. This is same for the your home and other networks. If someone establishes access to your network, they can monitor your activities.
Phishing attacks
Phishing attacks are used to cheat one target human to steal their private sensitive data. Attacker establishes a friendly relationship with their victims to phishing. Hackers can easily find your ISP by using your IP address. Using this ISP information hackers are allowed to run elaborate phishing attacks to steal personal data such as identity details, financial details, and more.
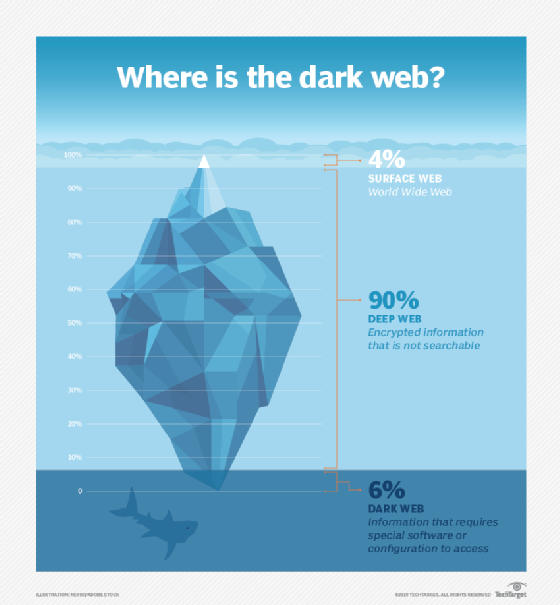
Sell sensitive data on the dark web
Alone, an IP address is not valued too much but when bundled with other sensitive data, it becomes very valuable. That information helps to identify you. Those can be usernames, location, social media information, financial information, or anything about you. Many data blockers, hackers, and scammers are waiting to buy these details for a price on the dark web.Hack your device
Only the IP address is not enough to hack a device. However, knowing your port numbers can impact your device or system. Every device has thousands of ports that do not have proper security measures, Attackers use various techniques to gain unauthorized access to the system using those ports. If they manage to connect to your device they can steal data on your system on implement malware on the device to continue their activities.
Frame you for crimes
Hackers and cyber criminals use hacked IP addresses for illegal activities they do not want to trace back. They could frame you to buy drugs, child pornography, or create security threats. If that illegal activity is caught by the government or other security organizations they can not find the real criminal, they caught you. because the hacker or criminal used your identity to do illegal things.
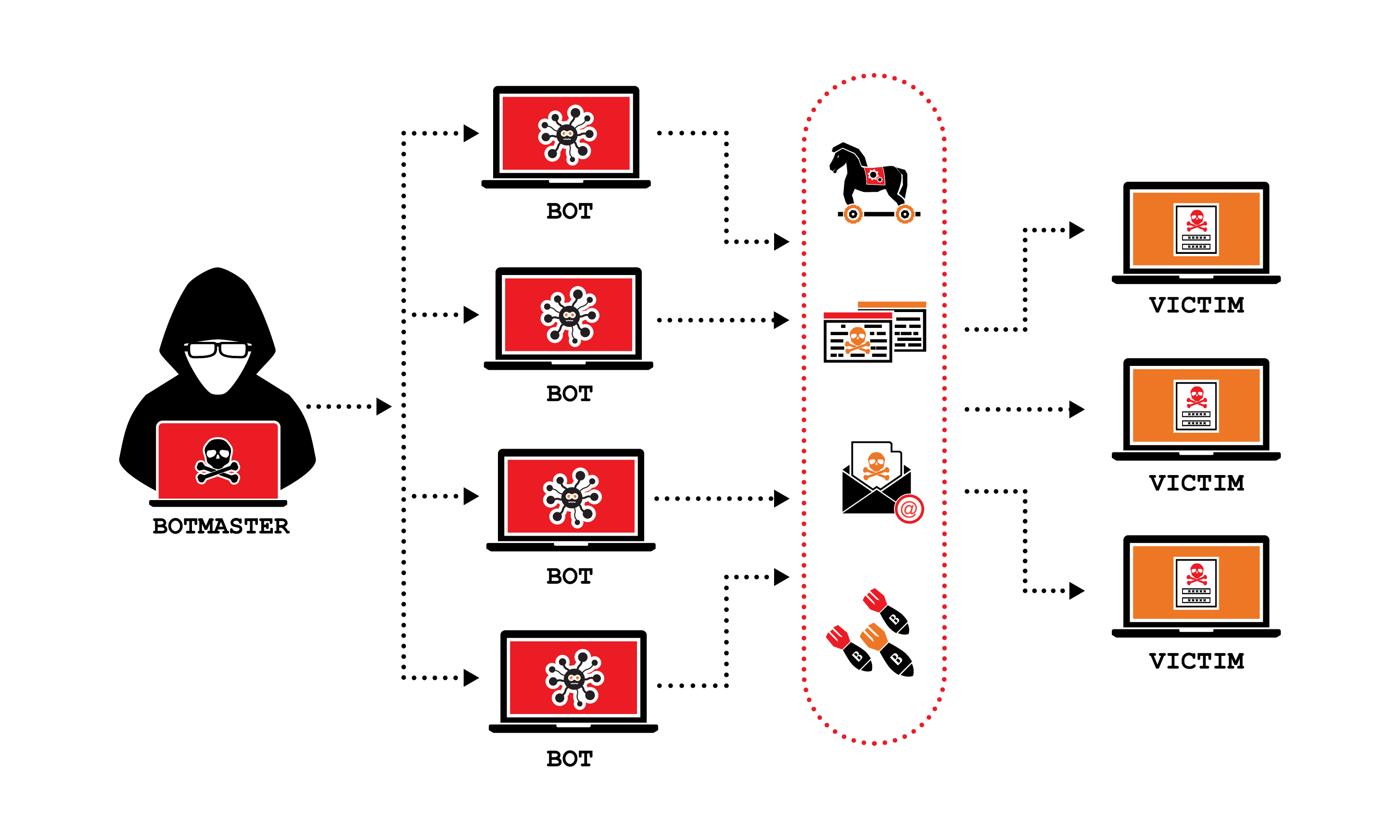
Execute DDOS attacks
Distributed denial of service attacks are used to flooring a network using internet traffic. Attackers generate and send a huge amount of requests to the target device until you can no longer access anything. They use botnet networks to generate that traffic at the same time. As a result of this traffic device starts lagging or freezing because it ran out of resources. finally DDOS attack shuts down the machine.
Read more: Top 6 tools in kali Linux
***






0 comments:
Post a Comment